I never planned to become obsessed with virtual queues.
It started as frustration. Turned into curiosity. Evolved into something I can only describe as an unhealthy fixation with understanding systems designed to keep me out.
Three years ago, I couldn't inspect a network request to save my life. Today, I've bypassed queue systems on four continents, across dozens of platforms, and developed techniques that most security teams don't even know to defend against.
This isn't a hacking tutorial. It's a confession.
Here's how a guy who failed his first computer science exam learned to walk past millions of people waiting in digital lines—and what it taught me about the fundamental fragility of modern web infrastructure.
The Spark
November 2021. A brutally cold Tuesday.
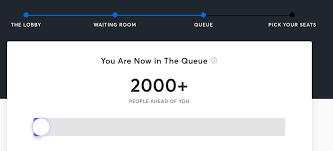
I was trying to buy a limited vinyl release from my favorite band. They'd announced a surprise drop—2,000 copies worldwide, hand-numbered, never to be repressed.
I'd been a fan for eleven years. Had their lyrics tattooed on my forearm. This was my grail.
The drop was scheduled for 3 PM GMT. I took a half-day off work. Set three alarms. Had the page loaded and ready by 2:45.
3:00:00 hits.
I click.
"Please wait. You've been placed in a queue. Estimated wait: 52 minutes."
My heart sank.
I watched the number tick down. 48 minutes. 39 minutes. 22 minutes. I started to hope.
Then: "Sorry, this item is now sold out."
I sat there for a long time. Longer than I'd like to admit.
Something broke in me that afternoon. Not dramatically—I didn't flip a table or swear revenge against the universe. It was quieter than that.
I just thought: How does this actually work?
And I opened the browser developer tools for the first time in my life.
Learning to See
The first month was humbling.
I didn't know what a network request was. Didn't understand cookies. Had never heard of an API endpoint. The developer console looked like hieroglyphics.
But I'm stubborn. Pathologically so.
I started with YouTube tutorials. Then documentation. Then forums where people discussed web scraping and automation. Slowly, painfully, the fog lifted.
I learned that websites aren't monolithic. They're collections of services talking to each other. Frontend talks to backend. Backend talks to database. Middleware sits in between, making decisions.
Queues are middleware.
They intercept your request before it reaches the actual website and decide whether you're allowed through. If you're not, they serve you a waiting room page instead of the real content.
But here's what fascinated me: queues don't see everything. They see what they're configured to see.
And configuration is done by humans.
Humans who make assumptions. Humans who forget edge cases. Humans who deploy on Friday afternoons and miss things.
That realization changed everything.
The First Win
Two months into my obsession, a streetwear brand announced a limited collaboration. The kind of thing that sells out in seconds and appears on resale platforms at five times the price.
I knew they'd use a queue. Everyone did by then.
But I'd been studying. Watching. Mapping.
For two weeks before the drop, I visited their website daily. Not to browse—to observe. I tracked every network request. Documented every endpoint. Built a map of their entire digital infrastructure.
Their queue was configured to trigger on product page URLs: /products/collab-*
Standard setup. Reasonable protection.
But I'd noticed something else. Their website had a wishlist feature. And the wishlist had its own API:
POST /api/wishlist/add
{"product_id": "collab-hoodie-black", "size": "L"}
Adding something to a wishlist shouldn't trigger a queue. It's a passive action. You're not buying anything.
But their wishlist API had a quirk. If the product was in stock and you were logged in with saved payment info, it returned a quick_buy_token in the response.
That token was valid for direct checkout.
No product page visit required. No queue trigger.
The day of the drop, I ran a script that polled the wishlist API every 200 milliseconds. The moment products went live, I had checkout tokens before the queue even knew items were available.
I got the hoodie. Size L. My size.
My hands were shaking when the confirmation email arrived.
Lesson learned: Queues protect specific paths. Every unprotected endpoint is a potential shortcut.
Going Deeper
That first success was intoxicating. But it was also lucky—I'd stumbled onto a misconfiguration specific to that one website.
I wanted to understand the underlying systems. Not just find bugs, but comprehend the architecture well enough to predict where bugs would exist.
So I went to the source.
The dominant queue provider publishes extensive documentation. They explain exactly how their system works—triggers, validation, token management, everything.
Most people never read it.
I read it three times.
Here's what I learned: queue systems are fundamentally reactive. They wait for specific conditions to be met, then intercept. The conditions are defined by rules. The rules are written by administrators who don't always understand their own applications.
Common trigger types:
- URL pattern matching — Queue activates when you visit certain pages
- JavaScript execution — Client-side code redirects you to the waiting room
- Cookie presence — Specific cookies indicate you need to be queued
- Header inspection — Certain request headers trigger interception
- Rate limiting — Too many requests too fast sends you to the queue
Each trigger type has weaknesses. Each weakness is exploitable.
The JavaScript Fallacy
Many queue implementations rely on JavaScript to function.
When you visit a protected page, the server returns the actual page content—but with a script that immediately checks your queue status and redirects you to the waiting room if you haven't been validated.
The logic looks something like this:
(function() {
if (!hasValidQueueToken()) {
window.location.href = '/queue/waiting-room';
}
})();
Simple. Effective. Fundamentally broken.
Because that code runs on your machine. In your browser. Under your control.
I learned to intercept JavaScript before it executed. Browser extensions. Proxy tools. Sometimes just disabling JavaScript entirely and seeing what happens.
One ticketing platform served their entire event page with the queue check in JavaScript. Disable scripts, and you got the raw page—complete with functioning "Buy Tickets" buttons.
The buttons worked.
They validated tickets server-side, sure. But they didn't validate that you'd completed the queue. The queue was purely cosmetic—a JavaScript redirect that accomplished nothing if you simply refused to run it.
I bought tickets to three shows that month using nothing more than Firefox's "Disable JavaScript" option.
Lesson learned: Client-side security isn't security. It's theater.
The Forgotten Endpoints
Modern web applications are archaeological sites.
Layer upon layer of code, accumulated over years. New features built on old infrastructure. APIs deprecated but never disabled. Endpoints that nobody remembers exist.
During one particularly deep dive, I found a retail website using three different checkout systems simultaneously:
- Their current React-based checkout (protected by queue)
- A legacy PHP checkout from 2018 (partially protected)
- An ancient mobile-web checkout from 2015 (completely unprotected)
The mobile checkout was still functional. It accepted the same product IDs, the same payment tokens, the same everything. It just lived at a different URL that nobody had thought to protect.
Current: checkout.example.com/cart
Legacy: example.com/checkout.php
Ancient: m.example.com/buy.php
I wrote a script that detected when products went live on the main site, then immediately submitted purchase requests through the mobile endpoint.
No queue. No waiting. Direct access to the order processing system.
This pattern repeats everywhere. Companies grow. Codebases expand. Security measures get applied to the new stuff but not retroactively to the old stuff.
Lesson learned: Always look for ghosts. Legacy systems haunt modern applications.
The Session Shell Game
Queue systems need to track who's waiting and who's been validated. They do this with tokens—unique identifiers stored in cookies or local storage.
The interesting question: what exactly do these tokens prove?
In theory, a token proves you waited your turn. In practice, tokens often prove much less.
I encountered a system where tokens were generated client-side using a predictable algorithm:
token = MD5(session_id + timestamp + "secret_salt")
The "secret" salt was hardcoded in the JavaScript. Anyone could read it.
By reverse-engineering the token generation logic, I could create valid tokens for any session at any timestamp. I didn't need to wait in the queue—I could simply claim I already had.
Another system used sequential token IDs. First person in line got token 1. Second person got token 2. And so on.
Validation checked if your token number was less than the "current serving" number. If current serving was 5000, tokens 1-4999 were valid.
I forged token 1. First in line. Immediate access.
Lesson learned: Token systems are only as strong as their generation and validation logic. Both are frequently weak.
Racing the Clock
This technique requires precision, but it's remarkably effective.
Queue systems don't activate instantaneously. There's always a delay—sometimes seconds, sometimes milliseconds—between when a product goes live and when the queue recognizes it needs protection.
I call this the "inception window."
For a major electronics drop, I studied their deployment patterns for weeks. Products consistently went live 2-3 seconds before the queue activated on their pages.
Milliseconds matter. But 2-3 seconds is an eternity.
I positioned scripts to hit their add-to-cart API the exact moment products appeared in their inventory system—which I could detect through a separate, unprotected stock-check endpoint.
My requests landed during the inception window. By the time the queue woke up, my items were already carted.
The technique requires:
- Precise timing
- Pre-positioned sessions with saved payment info
- Rapid execution (often sub-second)
- Redundancy (multiple attempts, multiple sessions)
It doesn't work every time. But it works often enough.
Lesson learned: Protection systems have startup latency. Speed kills queues.
The Geographic Lottery
Global companies run global infrastructure. And global infrastructure is hard to keep synchronized.
I discovered this during a sneaker release that launched simultaneously across multiple regions. The US site had a brutal queue—two-hour wait times. The UK site was similar.
But the Australian site?
Fifteen-minute queue. Minimal competition. Same products.
Even better: their Japanese site had no queue at all. They'd planned to implement one but hadn't finished the rollout.
I bought through Japan. Shipped to a forwarding service. Had the sneakers in hand ten days later.
This happens constantly. Security rollouts are phased. Marketing teams forget to coordinate with engineering. Regional variations slip through the cracks.
Lesson learned: Always check alternate regions. Global doesn't mean consistent.
The Referrer Trick
This one's almost embarrassingly simple.
Some queue systems decide whether to intercept you based on where you came from. Direct traffic to a product page? Queued. Traffic from the homepage or category pages? Allowed through, to prevent breaking the normal shopping experience.
The referrer is just an HTTP header. You control it completely.
Referer: https://www.example.com/homepage
I found a major retailer whose queue only triggered when the referrer was empty or from an external source. If your referrer indicated you'd navigated from within their site, you bypassed the queue entirely.
A single header modification. That's all it took.
Lesson learned: Headers are suggestions, not facts. Test what happens when you lie.
The Waiting Room Escape
Queue waiting rooms are web pages. They have JavaScript. They poll servers. They update your position.
And sometimes, they're the vulnerability themselves.
One implementation I studied polled a status endpoint every five seconds:
GET /queue/status?token=xyz
Response: {"position": 23481, "ready": false}
When ready became true, the JavaScript redirected you to the protected page with a completion token.
The completion token was generated server-side. But the redirect logic was client-side.
What happens if you send your own request to the completion endpoint without waiting for "ready"?
GET /queue/complete?token=xyz
The server checked if your token was valid. It didn't check if you'd actually waited. It just generated a completion certificate and let you through.
The queue was validating token format, not queue completion.
Lesson learned: Always probe the exit, not just the entrance.
The Shadow Cart
This technique requires patience and planning, but it's nearly undetectable.
Most e-commerce platforms let you add items to your cart before they're officially "released." The product exists in the database. The cart system accepts it. It just can't be purchased until the release time.
I learned to identify product IDs before official announcements—through URL patterns, API enumeration, even metadata in promotional images.
Days before a drop, I'd add items to my cart through direct API calls:
POST /api/cart/add
{"product_id": "unreleased-item-2024", "quantity": 1}
The cart accepted it. The item sat there, waiting.
When release time hit, everyone else started the journey: visit page, wait in queue, add to cart, checkout.
I skipped straight to checkout. My cart was pre-loaded. The queue protected the product page—not the cart I'd built days earlier.
Lesson learned: The purchase journey has multiple entry points. Pre-positioning can bypass the bottleneck entirely.
The WebSocket Dimension
HTTP isn't the only protocol in town.
Modern web applications increasingly use WebSockets for real-time features—live chat, instant notifications, collaborative editing, dynamic updates.
Queue systems monitor HTTP traffic. They often completely ignore WebSockets.
I found a ticketing platform where seat selection happened over WebSocket connections. The queue protected the HTTP endpoint for viewing available seats. But once you had a WebSocket connection established, you could select and hold seats directly.
{"action": "select_seat", "event": "concert-123", "seat": "A-15"}
{"response": "seat_held", "hold_token": "abc123", "expires": 300}
That hold token was valid for checkout. No queue required.
The trick was establishing the WebSocket connection early—during the pre-sale window, before the queue activated. Then maintaining it through the release.
Connection established. Seats selected. Queue bypassed.
Lesson learned: Different protocols, different protections. WebSocket is often the blind spot.
The Moral Weight
I need to reckon with something here.
These techniques have consequences.
Every queue I bypass, someone else waits longer. Every limited item I purchase through a backdoor, a genuine fan misses out. The math is zero-sum.
I've told myself stories. "I'm just one person." "The real scalpers use sophisticated bots." "If I don't do it, someone else will."
These are rationalizations. I know that.
The knowledge itself is neutral—understanding how systems work isn't inherently harmful. But application matters. I've used these techniques for personal purchases I genuinely wanted. I've also shared knowledge that others have weaponized for profit.
I can't unknow what I know. But I can be honest about its implications.
The queue exists for a reason. It's an imperfect attempt at fairness. Breaking it serves my interests at others' expense.
I'm not going to pretend otherwise.
What Actually Stops This
For the defenders reading this—here's what works:
Server-side validation for everything. Every decision that matters must happen server-side. Trust nothing from the client.
Comprehensive endpoint coverage. Map your own attack surface. Protect everything, not just the obvious paths.
Token binding. Tie queue tokens to device fingerprints, behavioral patterns, IP ranges. Make them impossible to forge or share.
Real-time anomaly detection. Humans have patterns. Bots have patterns. They're different patterns. Detect accordingly.
Protocol-agnostic protection. HTTP, WebSocket, GraphQL—queue logic should apply uniformly across all communication channels.
Legacy system audits. Find your ghosts. Disable or protect them.
Global deployment verification. Automatic checks that security measures are consistent across all regions and servers.
Conclusions
Three years of queue-breaking taught me things no textbook ever could.
I learned that security is an illusion maintained by mutual agreement. Systems trust you to follow the rules. When you don't, they often can't tell the difference.
I learned that complexity creates vulnerability. The more features a platform has, the more potential bypasses exist. Simplicity is security.
I learned that documentation is power. The answers hide in plain sight—in API docs, in framework guides, in the queue provider's own technical papers. Read everything.
I learned that timing matters more than almost anything else. The gap between deployment and protection. The milliseconds before a queue activates. The window between announcement and rollout. Speed is the ultimate bypass.
Most importantly, I learned that understanding systems changes your relationship with them. You stop being a passive user and become an active participant. You see the scaffolding behind the facade.
It's impossible to unsee.
That vinyl record I missed in 2021? I never got it. The moment passed. The band broke up a year later. The grail remains unattained.
But the obsession it sparked led somewhere unexpected. I understand the internet differently now. Not as a consumer, but as an explorer.
Every queue is a puzzle. Every waiting room is a challenge.
And somewhere, right now, someone else is sitting in front of a developer console for the first time.
Wondering how it all works.
Good luck.
The rabbit hole goes deep.




![Web Scraping with Gologin tutorial [2026]](https://cdn.roundproxies.com/blog-images/2026/01/gologin-1.png)