Most people think Ticketmaster is unbeatable.
They think the bots always win. They think regular fans don't stand a chance.
They think wrong.
What if I told you there's an old, forgotten system hidden inside Ticketmaster that could give you access to tickets before anyone else? What if adding 3,000 forward slashes to a URL could unlock presale codes meant for VIPs?
This isn't some dark web hack. It's a story about curiosity, persistence, and how ancient code can be your best friend.
The Ghost in the Machine
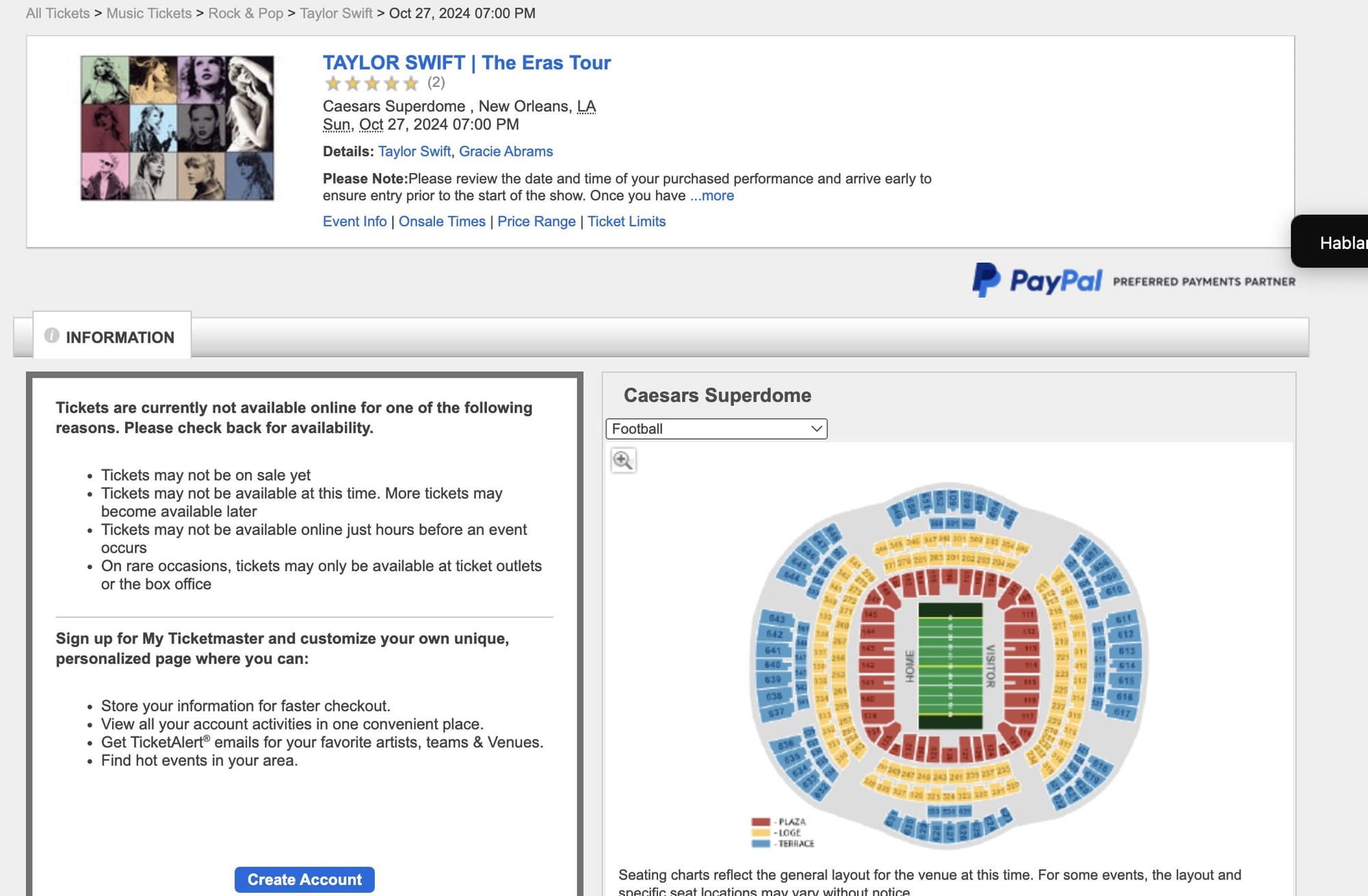
If you've ever tried to buy concert tickets, you know the drill. The countdown timer hits zero, you frantically click "Find Tickets," and... nothing. Sold out in seconds. Meanwhile, scalpers are already listing floor seats for 10x face value.
Here's what they don't want you to know: While everyone else is fighting over the modern Ticketmaster interface (the fancy GraphQL system called C02), there's an older system lurking beneath. I call it BBA — and until recently, it was wide open.
Think of it like finding a secret entrance to a sold-out venue. While thousands are crowding the main door, you're walking through the VIP entrance that everyone forgot existed.
How I Accidentally Broke Into Ticketmaster's Past
I wasn't looking for this. I was testing an old security bypass when something strange happened — an ancient product page appeared on my screen. It looked like Ticketmaster from 2005.
My first thought? This shouldn't exist.
My second thought? What else is hiding here?
The source code was a goldmine. It contained:
- Discount IDs (DIDs) that unlock hidden ticket allocations
- Presale information before public announcement
- Pricing data for tickets not yet released
- Rep names that could access any presale (minus unique passcodes)
But here's the crazy part — accessing this page didn't require sophisticated hacking tools or insider knowledge.
All it took was adding 3,000 forward slashes to the end of an event URL.
Yes, you read that right. Three thousand forward slashes.
The URL Overflow That Changed Everything
Here's how absurdly simple it was:
https://ticketmaster.com/event/0C00613EEDEC40C8//////////... (repeat 3,000 times)
This technique, called URL Overflowing, bypassed Ticketmaster's security measures (specifically Incapsula/reese84 cross-site protection). It's like finding out you can unlock a high-security door by jiggling the handle really, really hard.
The bypass worked because security systems often have length limits on URLs they check. By overwhelming the system with slashes, I essentially made it give up and let me through.
Why this matters: Those discount IDs I found? They're usually sent via exclusive emails or third-party signups.
Having them meant accessing ticket allocations reserved for credit card presales, fan clubs, and VIP packages — without actually being a member.
When One Door Closes, Google Opens Another
Ticketmaster eventually patched the trailing slash exploit. Game over? Not quite.
I remembered an old trick from my security research days: Major websites rarely block traffic from search engine crawlers. It's bad for SEO, and nobody wants to anger Google.
So I tried the Google AdSense tester. Here's the beautiful part — Google doesn't validate which domains you test. I reported this to their bug bounty program, but apparently, it "wasn't important enough." Their loss, my gain.
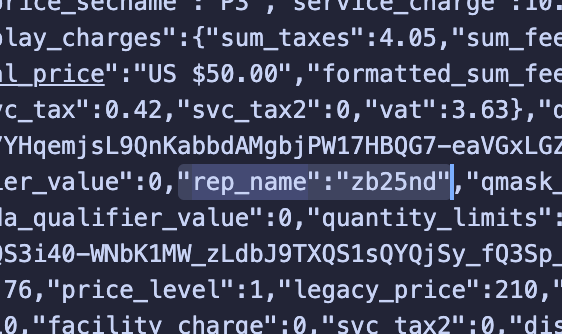
The AdSense tester accessed the page, but there was a problem. It rendered everything as HTML, stripping out the JSON data I needed. The crucial rep_name values were gone.
Time for Plan C.
The Schema Validator Backdoor
Every modern website uses something called Schema markup. It's structured data that helps search engines understand your content. You've seen the results — those rich snippets in Google with star ratings, prices, and event dates.
Ticketmaster uses Schemas extensively for SEO. And where there's SEO, there's usually a way in.
I found Schema.org's validator tool: https://validator.schema.org
Here's what happened:
- I pasted my bypass link with trailing slashes
- The validator bypassed Ticketmaster's security (it needs to access the page to validate it)
- It showed me the complete source code
- All the hidden data was visible again
For a brief, glorious period, I had full access to presale information, discount codes, and ticket allocations for any event on Ticketmaster.
Why This Worked (And Why It Matters)
This wasn't about sophisticated hacking. It was about understanding how systems talk to each other and finding the gaps between them.
The key principles:
- Old systems often have weaker security
- Security tools make exceptions for "trusted" services
- Complex systems have more attack surfaces
- Sometimes the simplest exploits are the most effective
What you could do with this access:
- See which presales were coming before announcement
- Find discount codes meant for specific groups
- Access ticket allocations others couldn't see
- Check real pricing before dynamic pricing kicked in
The Lessons for Your Own Adventures
You don't need to be a coding genius to find these exploits. You need:
Curiosity over complexity: I found this by accident while testing something else. Stay curious about how things work.
Persistence over perfection: When the first method was patched, I found another. Then another. There's always another way.
Understanding over exploiting: Know why something works, not just that it works. When you understand the principle, you can find new applications.
Document everything: These windows close fast. When you find something interesting, document it immediately.
The Bigger Picture
Ticketmaster patched these specific exploits, but the principles remain. Every large system has legacy code. Every security measure has exceptions. Every wall has a door — you just need to know where to look.
The real lesson isn't about beating Ticketmaster. It's about questioning assumptions. Everyone assumes these systems are impenetrable. Everyone assumes you need sophisticated tools and insider knowledge.
Everyone assumes wrong.
Sometimes, all it takes is 3,000 forward slashes and a willingness to try something ridiculous.
This article is based on a thread shared over here .







![IPRoyal vs Oxylabs: Which provider is better? [2026]](https://cdn.roundproxies.com/blog-images/2026/02/iproyal-vs-oxylabs-1.png)

